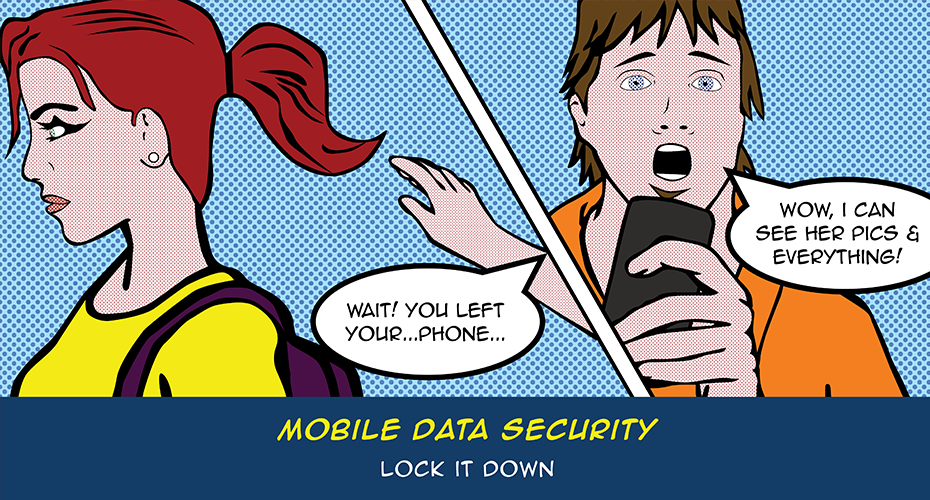
Secure Mobile Data Against Loss, Theft and Unauthorized Access
Laptops, smartphones, and removable storage drives enable us to get information on the go. We no longer have to be tethered to our desks to check our email, surf the web, or access files and information. Advances in wireless communication have made communication mobile, but also made it easier for the unscrupulous to access our personal information. Unless you secure your mobile data against loss, theft and unauthorized access, you are vulnerable.
How can you protect your mobile data?
- Encrypt off-campus Wi-Fi transmissions using the Auburn VPN when possible.
- Secure your USB Drive
- Don't leave them behind in public labs
- Truecrypt - 3rd Party encryption method for removable storage
- Wikipedia article on securing your USB drive - Use BitLocker To Go - this feature of Windows 7 gives the lockdown treatment to easily-misplaced portable storage devices like USB flash drives and external hard drives. This allows you to protect information stored on removable media with the same level of protection as the operating system volume.
- Secure your laptop - don't make it easy for the bad guys: use a carrying case that does NOT look like a laptop bag and don't leave your laptop unattended. In the AU Library you can check out a lock for your laptop so you don't have to take it with you to the stacks. Taking things one step further, password protect your laptop and consider installing tracking software.
- Secure your handheld device - your smartphone and tablet can be protected by simply setting a password on the device.
Additional Helpful Links
- Cybersecurity for Electronic Devices
- Protecting Portable Devices
- Physical Security for Your Cell Phone or Smartphone
What to do if you lose your phone
Login to TigerMail online and go to Options > See All Options > Phone and select your device. Choose Wipe Device. Wait ten minutes, then contact your wireless provider to disable the phone.
If you were using your phone to check any email account via IMAP, change your password for that account. This will not remove the existing email from the phone, but it will prevent future nefarious usage of the account(s).
If you are an employee on the Blackberry Enterprise Server (BES) follow these steps:
- Immediately contact OIT by calling the HelpDesk at (334) 844-4944 or sending an email directly to besadmin@auburn.edu (Exchange Blackberry users). We can wipe out the data on your phone remotely. It can be restored later, but whoever finds your missing phone won't be able to read all of your email and other sensitive data in the meantime.
- Once OIT has verified the hard reset of your phone's data, call your service provider and disable the phone number so unauthorized calls cannot be made.
Don't reverse these steps. Once the phone is disabled, OIT won't be able to access it to perform step #1.
Wireless Safety in Public Hot Spots
People in Auburn have embraced the use of wireless networks. Unfortunately, online predators know this too. Using unsecured wireless networks can leave you computer, phone and handheld devices vulnerable to attack. Here are some tips when using a wireless network:
- Only use legitimate hotspots (wireless access points) - make sure you know who owns the connection you are trying to access.
- Use a VPN client - Download a free VPN client at AU Install.
- Enable your personal firewall - Microsoft Windows users have a personal firewall installed.
- Turn off your Android/iPhone's built-in Wi-Fi when you aren't using it or you may be auto-connecting to nearby wireless access points - plus it saves your battery!
- Don't forget to secure your wireless network at home by enabling a password for the wireless router. If you are in an area with many wifi hot spots or lots of residents near your wifi consider not broadcasting your SSID.

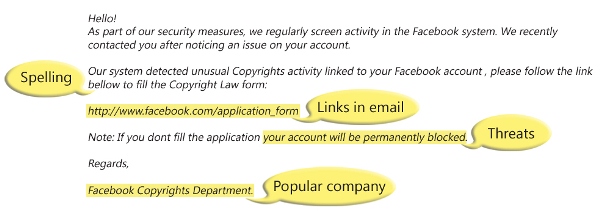
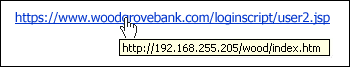





Once Your Personal Info Is Online, It's There
Web sites want personal information because it helps them build community and enables them to provide advertisers with demographic information about their members, but whether to share those details is your decision.
Bottom Line: the more personal information you reveal online, the more vulnerable you are to scams, spam, and identity theft.
Don't Be a Victim
Let's face it. Do you really think that super hot girl is having trouble meeting people? Chances are it's some scumbag trying to get your personal information to commit identity theft.